China Removes 'Green Dam'
In a very unexpected move, the Chinese authorities have indefinitely postponed their order that all PCs sold in the country must come with software, called Green Dam Youth Escort, that blocks certain websites.
According to Reuters, Chinese artist and activist Ai Weiwei, who had previously organized a protest against the Green Dam initiative, has also called on the people of China to celebrate its demise. About 200 Beijing residents, dressed in t-shirts mocking Green Dam, have arrived at a trendy art zone cafe to party all day in celebration of this victory in a war against censorship.
The Chinese authorities were under a great deal of pressure from various trade groups, American, European and Japanese chambers of commerce, and the U.S. National Association of Manufacturers, which sent a letter of protest against the measure, claiming it “raises significant questions of security, privacy, system reliability, the free flow of information and user choice.”
The combination of a huge public outcry against Green Dam and the reluctance of PC sellers to comply probably wouldn’t have been enough to convince the Chinese government to give up on Green Dam, but the fact that this measure was obviously undertaken in haste, with Green Dam itself having some serious issues (it doesn’t, for example, support 64-bit operating systems), was probably the straw that broke the camel’s back. In a word, Green Dam was not only unpopular; it was nearly impossible to implement.
Unfortunately, however important, this victory is a minor one. The Green Dam initiative was only postponed by the The Ministry of Industry and Information Technology; it could be reinstated at a later date. Even more importantly, Chinese Internet users are still behind the iron veil of the Great Firewall of China, which blocks them from visiting certain websites, with the blockade often spreading to the most popular internet destinations. I hope that the Chinese authorities have really softened up when it comes to censorship, but I fear that this might only be a minor drawback in their quest for total control of the Chinese Internet.
5:15 PM | Labels: Internet | 0 Comments
Search Options now in Google Images
A few months ago when we announced the Search Options panel, we promised that you would soon see similar functionality across our other search properties. Today we are rolling out Search Options for Google Images.
This new feature offers quick access to existing tools, including search by color and image type. Color search will find images that are only in color or only in black and white, or even images that contain a specific color, such as red, pink, or green. Type search is a great way to narrow down your results if you are looking for a specific kind of image, such as a photo, clip art, line drawing or face.
We've also revamped our size search. In addition to choosing from commonly searched-for sizes, now you can search for an exact image size or any image larger than a certain size. You can find images of practically any size, including 70 megapixels or more.
The new layout makes it faster and easier to combine and toggle between options. It also makes it easier for us to add additional image search options in the future, so keep your eyes peeled. Just click "Show options..." in the blue bar on the search results page to try out any of these tools.
Source:Google Blog
5:10 PM | Labels: Google | 0 Comments
Lock your Pen drive
Data protection is a function of both deletion and encryption:
Deleting data does not necessarily remove the information from your drive. Usually, when deleting files only the pointer to the file in the file allocation table is deleted, leaving the files actual data untouched. This enables hackers to undelete files using special utilities.
In order to encrypt your data, it has to be read, encrypted and then replaced by the new encrypted data. This means that your original file is deleted and replaced by an encrypted version of the same file. Therefore the deleted original can be retrieved as explained above. Encryption alone is not completely safe.
In order to protect your data, it must be encrypted, in addition to physically wiping any trace of your original un-encrypted files. This is exactly what Lockngo Professional does.
Features:
Military Grade 256bit AES Encryption (FIPS 140-2 Certified)
Lockngo encrypts your files in extra strong ecryption making sure your data can't be compromised.
No software installation required
Lockngo runs directly from your removable media - does not require installation on any PC.
Fast encryption
Ultra-fast encryption optimization to reduce lock/unlock time.
Hides your files
Data is not only encrypted, but also hidden so it is completely impossible to retrieve.
Rich file-system support
Lockngo Professional now supports NTFS (New), FAT32 and FAT file systems.
New! Instant Lock
Lockngo Professional now provides a new, even quicker workflow, enabling you to lock the drive in one simple click.
Command Line control, advaced administration
Lockngo Professional offers control and configuration of its features right from the command line, enabling access to functionality and settings not available to the common user. The command line enables system administrators to permanently modify the software's settings and make the lock operation faster (removing the need to enter password each time). Command line access also assists system administrators seeking to manage multiple portable drives in their organization.
Remembers your password
Lockngo Professional remembers your password which makes your next use even easier.
Download Lockngo
11:43 AM | Labels: USB | 1 Comments
Mobile Manufacturers agree on standard phone charger
Some of the world's biggest mobile phone manufacturers have agreed to adopt a new universal standard of phone charger in an effort to be more environmentally friendly.
Until now, most mobile phones have used proprietary chargers that will only work on one kind of device, leading to cupboards full of unwanted chargers in homes across the country.
But now, according to a report in The Telegraph, ten companies, including Apple, LG, Nokia, Samsung and Sony Ericsson, have submitted a Memorandum of Understanding to the European Commission pledging to start making phones that can be charged using a single charger.
The manufacturers will adopt the Micro USB connector across all their devices from next year, meaning that dozens of different handsets can be charged using a single plug.
The European Commission has been putting pressure on mobile phone makers to reach an agreement on a universal charging standard in an effort to cut down on the thousands of tons of waste generated each year by the inclusion of unwanted chargers with every new handset.
The GSMA, the trade organisation that represents the mobile phone industry, said that the new universal chargers will consume half as much energy when on standby as today's charging cables.
Technology experts have welcomed the announcement.
Source: Yahoo News
11:53 AM | Labels: Mobile | 3 Comments
Microsoft releases Silverlight 3
Microsoft has released the latest version of its Silverlight player.
The release of Silverlight 3 arrived late Thursday night. The company’s presentation technology for graphics and video on the web was supposed to be released to the public on Friday morning, July 10 — there’s even a lavish launch event scheduled at a San Francisco hotel — but Microsoft decided to push Silverlight out a day early.
Silverlight 3 is a small, free plug-in download from Microsoft. It’s cross-browser and cross-platform, so it runs on Windows, Mac (the newest versions are Intel only) and Linux computers. The open-source Linux version is called Moonlight, and it ships with Novell distributions. If you’re running Ubuntu or some other non-Novell distribution, you can download it and install it manually.
Silverlight is Microsoft’s plug-in based player for streaming video and audio content, handling rich internet apps and displaying animated user interfaces in the browser — Redmond’s answer to Adobe Flash and open-source technologies like those promised by HTML 5. When Silverlight first arrived in 2007, it didn’t run too well on non-Windows desktops. Worse, with very little content available on the web for Silverlight to play, there wasn’t much of a reason to bother with it.
But quite a bit has changed in two years. Most notably, the compelling content finally arrived. Microsoft streamed live video and highlight clips on NBC’s official Beijing Olympics website in the summer of 2008 using Silverlight. The company released version 2 in September of 2008, an upgrade which improved Silverlight’s performance on Macs and improved the video playback quality overall. Silverlight was used again to stream coverage of the 2008 Democratic National Convention and all of the NCAA March Madness basketball tournament games in 2009, serving to raise Silverlight’s profile — and it’s install base — even more.
By now, Silverlight is installed on around 30% of web-connected PCs and devices like Windows Mobile smartphones. It’s a far cry from Adobe Flash’s install base (which is over 90%) but it’s a significant gain in a short period of time nonetheless. Also, Microsoft claims there are over 300,000 developers actively building web sites, apps and animated user interfaces in Silverlight right now.
Silverlight’s video capabilities have always been impressive when compared to Flash, and the new version boasts some new features that should keep the competition with Flash hot. It uses a media broadcasting technology Microsoft calls Smooth Streaming, an adaptive technology for playing the same H.264 video stream at the highest bitrate the device and its bandwidth limitations will allow. So if you’ve got a fast computer with an HD monitor and a wide open pipe, you’ll see super high quality video at up to full 1080p HD. If you’ve got a dinky smartphone with mid-level data service, you’ll see a constrained version of the same video.
The new version of Silverlight also has better 3-D graphics support and the ability to offload graphics work to a GPU for a smoother, hardware-accelerated user experience.
On the rich internet apps front, Silverlight 3 includes the ability for developers to create apps that run outside of the browser on a PC desktop, or on a mobile phone — yet another place where Silverlight 3 is catching up to competing technologies like AIR, Adobe’s Flash-based runtime for running webapps outside of the browser.
Also due to be released Friday (but not showing up yet, as of this writing late Thursday night) is Expression Studio 3, Microsoft’s set of tools for building Silverlight apps, standards-based websites and vector graphics for the web. The current version, Expression Studio 2, costs $700, or $350 for an upgrade from previous versions.
As mentioned previously, the Silverlight browser plug-in is free.
Silverlight Update Aims for Greater Adoption Through Developers
Mozilla Brings Webapps to the Desktop, Challenges AIR, Silverlight
Microsoft Launches Silverlight With Full Linux Support
Source: Webmonkey
4:09 PM | Labels: Microsoft, Software | 0 Comments
NVIDIA unveils Tegra
Amidst the hype about Intel's processor platform for MIDs called Moorestown, NVIDIA has unveiled an answer of its own, its Tegra Processor.
They unveiled 12 high definition capable MIDs powered by the Tegra chip which are capable of delivering a desktop like browsing experience complete with Flash. As can be expected of any NVIDIA product, it has powerful graphics support with animation acceleration, flash video support, and the capability to play back video at full 1080p.
Since it is targeted for portable devices, it is also optimized greatly for lower power usage and may give as much as 5 times the battery life that we can see in the netbooks of today. It is capable of 25 days of playing music on a single charge, and 10hrs of full HD 1080p video playback.
According to Michael Rayfield, general manager of mobile business at NVIDIA, “These new Tegra-based products combine excellent Internet and media capabilities, always-on operation, and wireless connectivity for the un-tethered Internet experience consumers have been craving.”
In order to have a desktop-like browsing experience, support for Adobe Flash is necessary. For this NVIDIA tied up with Adobe to optimize the Flash Player for Tegra, by enabling it to utilize the powerful GPU of Tegra based devices to make the online Flash video and animation experience as smooth as possible. The Tegra architecture utilizes multiple processors working in unison for giving the composite experience. A separate processor is used to processing HTML, and HD video.
With the capability to support 3G, WiFi and WiMAX it also welcome by wireless carriers. As stated by Antonio Domit, Executive Technology Advisor to America Movil, Grupo Carso, and Inbursa, “Devices based on NVIDIA Tegra will allow us to offer a mobile Internet device that delivers an amazing level of functionality at minimal cost or even free through subsidies, The combination of a Tegra-based MID and our high-speed national coverage will allow millions of people to access the Internet and have an unprecedented experience. I can imagine the story is the same for every country around the world.”
Tegra devices are expected to start coming out in the second half of this year.
Source: Digit
4:09 PM | Labels: Hardware | 0 Comments
Google planning to introduce a Operating System
It's been an exciting nine months since we launched the Google Chrome browser. Already, over 30 million people use it regularly. We designed Google Chrome for people who live on the web — searching for information, checking email, catching up on the news, shopping or just staying in touch with friends. However, the operating systems that browsers run on were designed in an era where there was no web. So today, we're announcing a new project that's a natural extension of Google Chrome — the Google Chrome Operating System. It's our attempt to re-think what operating systems should be.
Google Chrome OS is an open source, lightweight operating system that will initially be targeted at netbooks. Later this year we will open-source its code, and netbooks running Google Chrome OS will be available for consumers in the second half of 2010. Because we're already talking to partners about the project, and we'll soon be working with the open source community, we wanted to share our vision now so everyone understands what we are trying to achieve.
Speed, simplicity and security are the key aspects of Google Chrome OS. We're designing the OS to be fast and lightweight, to start up and get you onto the web in a few seconds. The user interface is minimal to stay out of your way, and most of the user experience takes place on the web. And as we did for the Google Chrome browser, we are going back to the basics and completely redesigning the underlying security architecture of the OS so that users don't have to deal with viruses, malware and security updates. It should just work.
Google Chrome OS will run on both x86 as well as ARM chips and we are working with multiple OEMs to bring a number of netbooks to market next year. The software architecture is simple — Google Chrome running within a new windowing system on top of a Linux kernel. For application developers, the web is the platform. All web-based applications will automatically work and new applications can be written using your favorite web technologies. And of course, these apps will run not only on Google Chrome OS, but on any standards-based browser on Windows, Mac and Linux thereby giving developers the largest user base of any platform.
Google Chrome OS is a new project, separate from Android. Android was designed from the beginning to work across a variety of devices from phones to set-top boxes to netbooks. Google Chrome OS is being created for people who spend most of their time on the web, and is being designed to power computers ranging from small netbooks to full-size desktop systems. While there are areas where Google Chrome OS and Android overlap, we believe choice will drive innovation for the benefit of everyone, including Google.
We hear a lot from our users and their message is clear — computers need to get better. People want to get to their email instantly, without wasting time waiting for their computers to boot and browsers to start up. They want their computers to always run as fast as when they first bought them. They want their data to be accessible to them wherever they are and not have to worry about losing their computer or forgetting to back up files. Even more importantly, they don't want to spend hours configuring their computers to work with every new piece of hardware, or have to worry about constant software updates. And any time our users have a better computing experience, Google benefits as well by having happier users who are more likely to spend time on the Internet.
We have a lot of work to do, and we're definitely going to need a lot of help from the open source community to accomplish this vision. We're excited for what's to come and we hope you are too. Stay tuned for more updates in the fall and have a great summer.
Source: Google Blog
3:41 PM | Labels: Google | 0 Comments
Kaspersky Lab and BitDefender websites hit by hackers
The websites of two major providers of security products have been hit by hackers.
The website of Russian IT security provider Kaspersky Lab was hit at the weekend by a Romanian ‘white-hat’ hacker.
A group calling itself ‘the Romanian Security Team’ claimed that the hackers achieved full access to the database supporting the websites – which includes customer data – by simply altering a parameter in the URLs. They could also perform SQL injections to remotely introduce harmful code into the database.
The group also claimed to have hit the Portuguese site of US anti-virus provider BitDefender, with the personal details of thousands of users viewed. The hackers said that they alerted the two companies of the security flaw and did not expose any of the data they found.
Kaspersky Lab said in a statement: “On Saturday February 7 2009, a vulnerability was detected on a subsection of the usa.kaspersky.com domain when a hacker attempted an attack on the site.
“The site was only vulnerable for a very brief period, and upon detection of the vulnerability we immediately took action to roll back the subsection of the site and the vulnerability was eliminated within 30 minutes of detection. The vulnerability wasn’t critical and no data was compromised from the site.”
Gunter Ollmann, chief security strategist at IBM’s Internet Security Systems, said: “I hope that Kaspersky administrators fix this vulnerability rather quickly as they no doubt have a large customer base, and it would appear that all those customers are now exposed
“On top of that, this type of critical flaw can probably be used to usurp legitimate purchases and renewals of their products - which could include the linking to malicious and backdoored versions of their software - thereby infecting those very same customers that were seeking protection from malware in the first place.”
9:28 PM | Labels: News, Security | 0 Comments
How to Rip a DVD to an AVI or MPEG File
1. Download DVDx archive file to your computer (DVDx_2_10_setup.zip), open it and double-click on "DVDx Setup". Complete the installation of DVDx.
- Ensure you have XviD (and/or DivX) drivers by installing AutoGK or downloading codecs separately.
- Download the latest Avi Rip free from Avi Rip
- Download the latest DivX free from divx.com
2. Now run the DVDx software. The program window will appear.
You should insert the DVD you wish to rip into the DVD drive. Alternatively, if your DVD is saved as files on your computer, you can rip from there.
On the DVDx window, there are three menus available, File, Settings, and Tools.
A file window opens, and you can browse to your DVD.
Alternatively, to open DVD files which have been previously saved to your hard drive, click "Open IFO" to select your hard disk files as source.
In the folder selection box, select the file VTS_01_0.IFO in the DVD target directory on the hard drive.
 Your movie is now loaded as source.
Your movie is now loaded as source.
The Input Settings dialog automatically opens.
3. If you have more than 1 movie on the DVD, select the file that shows up in the popup box and then choose which movie you wish to encode by selecting it from the pull down menu in the upper left corner. You will have to choose the root menu and file for each one on the DVD, if there is more than 1 movie on the DVD.
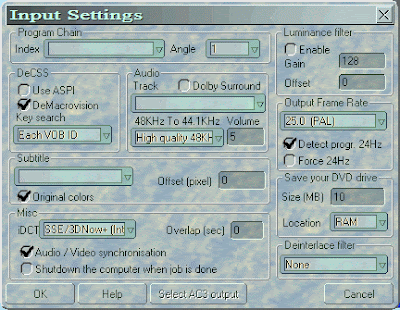 4. Notice that the Input Settings dialog will show, in the Program Chain Index section at top left, the length of the movie to be processed. Check a suitable audio track is shown in the Audio section.
4. Notice that the Input Settings dialog will show, in the Program Chain Index section at top left, the length of the movie to be processed. Check a suitable audio track is shown in the Audio section.
- Other settings can be left at default.
- Note: If during conversion you get an error "DVD drive could not be locked", you should install ASPI drivers, and then select the "Use ASPI" option. Otherwise this will not be necessary.
- Now click OK.
6. Change several settings in the Output Settings dialog box:
- Choose an output format (AVI is suitable for playback in Media Player).
- Now choose an audio compression method. Lame MP3 is capable of excellent sound at small filesize (AVI only). If Lame is not available, choose the MPEG video compression, or download Lame MP3 drivers.
- Choose the XviD video codec in the dropdown menu. Click 'Enable Video', but leave 'Enable 2nd' unchecked. You can choose an alternative video codec (such as DivX or Mpeg4) if you prefer.
- Across in section Export Settings, choose a screen size (resolution) for encoding.
- For widescreen monitors (size ratio 16:9) choose 720x576. Any multiple of 16 is acceptable.
- For normal monitors choose (size ratio 4:3) choose 720x544. Any multiple of 16 is acceptable.
- Next to the Max Frame number, click the button named Whole. Make sure you press this button for each new DVD movie or DVD file that you choose.
- Other settings can be left at default.
- Click the Apply button.
- Browse to a suitable destination folder, and type a filename into the box. Click on Save, then OK.
- You are now ready to convert a DVD to an AVI.
10. Wait for encoding to complete and then enjoy your movie.
Source:WikiHow
Read the rest of this entry >>
8:43 PM | Labels: DVD, Movies | 0 Comments
Find out if your email has been read
Now you can find out when your email has been read by the recipient! No more guessing: "Has he or she read my email yet?"
SpyPig is a simple email tracking system that sends you a notification email as soon as the recipient opens and reads your message.
It works with virtually all modern email programs: Outlook, Eudora, Yahoo Email, Gmail, Hotmail, AOL Email and many others.
Best of all, SpyPig is FREE! No spam, no virus, no adware, no spyware. You can use it as often as you like, and there's no catch. Just introduce the Pig to all your friends! The system is very easy to use. In just few minutes, you'll be able to use it like a real spy!
Use It with Classified Ads
SpyPig is especially useful when you respond to a classified ad such as that on Craigslist (for an employment, for example) and wonder if your email reaches its target.
Basic Requirement
Both you and the recipient must use an HTML email, not plain-text or rich-text email. Visit the Requirements & Limitations page to learn more about SpyPig.
For more details, visit SpyPig
8:40 PM | Labels: Internet | 0 Comments
USB Vaccine
Panda has released Panda USB Vaccine with NTFS Support. It is out of it's beta stage and a full version has been released (v.1.0.0.50).
Some of the most notable improvements are the following:
- Support for vaccinating NTFS drives. This uses a completely different technique than the vaccination of FAT/FAT32 drives.
- Executing USBVaccine.exe launches an installer which allows you to configure whether you want USBVaccine to start automatically with Windows.
- Configuration option during setup to hide the tray icon.
- Configuration option during setup to automatically vaccinate any new USB drives inserted into the PC.
- Fixed bug on PC shutdown when USBVaccine was running in the background (Vista).
- Other bug fixes reported by users on certain types of USB drives.
The download is available on CNET here.
Read the rest of this entry >>
11:40 AM | Labels: Antivirus, USB, USB virus | 0 Comments
Pirate Bay acquired for $7.7 Million
The Pirate Bay team which recently went to court and loss for copyright violations, has launched a brand-new site called VideoBay. Video Bay provides streaming content of TV shows, music videos and more.
The new video streaming site is definitely still in beta, perhaps even alpha, because the site comes with a warning that states, "Don't expect anything to work at all". The on-going development of the site will take up to several years according to Peter Sunde of Pirate Bay.
In other news, a Swedish based technology company that goes by Global Gaming Factory X said that it had reached an agreement with The Pirate Bay to acquire it for $7.7 million. After the acquisitions the new owners would bring a legitimate business model to the Pirate Bay.
How the new owners plan on turning something such as the Pirate Bay into a legitimate business is beyond me. Doing so, would probably make them loose many users - and recouping their costs nearly impossible. However, with them investing that kind of money in something they most definitely have a business plan on how to accomplish it all. It will just be interesting to see how it plays out.
"We would like to introduce models which entail that content providers and copyright owners get paid for content that is downloaded via the site" said Hans Pandeya, CEO of GGF.
Okay, so they apparently want to do paid content but what would the content be? If it's not "open for anything" like the way it is now days, it's going to be hard to retain users IMO. Most of the users will go elsewhere anyway and you gotta think that GGF knows this as well. When users go to a site expecting something free, it's going to be hard to make them start paying when they can go down the road to the next house and get it free there.
"The Pirate Bay is a site that is among the top 100 most visited Internet sites in the world. However, in order to live on, The Pirate Bay requires a new business model, which satisfies the requirements and needs of all parties, content providers, broadband operators, end users, and the judiciary. Content creators and providers need to control their content and get paid for it. File sharers' need faster downloads and better quality" continues Hans Pandeya.
I hope it plays out well for the new owners. If they could somehow purse enough owners of content to continue allowing their material on the Pirate Bay, it might just work. I think that is definitely an uphill battle though.
Soure:Tech Fragments
8:01 PM | Labels: Torrent | 0 Comments
Fastest Browser yet
The folks at Mozilla have deemed the changes in this incarnation of the popular Firefox browser significant enough to skip the planned version 3.1 and instead bump up the release number to 3.5. And I agree—it's a big improvement. By its appearance, you'd be hard pressed to tell how Firefox 3.5 differs from 3.0, but it's what's inside that counts. The new version speeds up JavaScript performance and catches up with other recent browsers like Internet Explorer 8, Opera 10, and Safari 4 by adding a private browsing mode. And 3.5 builds on everything you everything that made the previous versions of Firefox great, like the myriad extensions and themes and the "awesome" address bar for quickly getting where you're going on the Web. The result? An impressive piece of software gets even better.
I like Firefox 3.5's new New Tab button, which takes a page from Internet Explorer and Opera's playbook with a plus sign that makes it more obvious how to add a new tab. You can also now grab a tab and drag it into a new window on the desktop—or drag a window back into the open browser. The page appears as a large thumbnail while you do this. Safari, Chrome 2, and Opera all can do this, but IE8 still can't. Firefox is the last holdout to offer only a blank white page on new tabs: All other modern browsers display history, recently closed tabs, and favorites. Finally, in an appealing new touch, when you open a new tab in Firefox 3.5, the existing ones slide to the left.
Firefox already had an "Open recently closed tabs" choice, but 3.5 can reopen recently closed windows, too, so even if you've closed a whole browser window you haven't lost its tabs.
Buzz up!on Yahoo!
Unlike most of the competition, Firefox displays no indication when you're in the new private browsing mode—IE shows an InPrivate graphic in the address bar, and Chrome displays a private eye icon. When you start Firefox's private browsing mode, your existing tabs disappear, but they return when you turn off the mode. I had to reconnect to Outlook Web Access after a private session, though I'd been logged in before. Nothing from my private session appeared in history or in the awesome bar, which is how it should be.
You can also have the browser forget any site in your history. A new twist in clearing private data is that it's no longer an all-or-nothing proposition: Firefox 3.5's Clear Recent History lets you tell the browser just to clear history, cache, cookies, logins, and so on for the past hour, two hours, four hours, or whole day, or for your entire history. This is more control than the old Clear Private Data offered.
One nitpick of mine is that the sidebar isn't as accessible as the ones in Internet Explorer and Opera, which offer button access. This handy panel can show history or bookmarks, but you can only get to it if you know the keyboard combination, by customizing your toolbars, or by choosing it from the View menu. In Opera, the sidebar performs a multitude of functions as well, such as downloads, notes, and widgets.
Source: PC Mag
Download Firefox 3.5 RC
7:40 PM | Labels: Firefox | 0 Comments
An easy way to find out when your last reboot was
Method 1: Windows NT/2000 and XP
Open command prompt
Go to Start ---> Run--->
Now type cmd.
When the command prompt has loaded, type “net stats srv” (or “net statistics server”).
Method 2: Windows XP and beyond
In command prompt, type “system info” which will also provide you with your PC’s uptime.
Method 3: Windows Vista and beyond
For those using Vista or Windows 7, right click the taskbar and choose “Task Manager” or “Start Task Manager”. Click “Performance” tab and on the bottom right of the window you can see your system uptime.

3:42 PM | Labels: Tweaks, Windows | 1 Comments
Zemanta to make your blog better

Here's how it works: while you write your blog post in Blogger, Zemanta opens up a sidebar next to the Blogger post editor. After you've written a few sentences, Zemanta analyzes the words in your post and suggests images and video that are relevant to your post; with one click, it inserts them into your post. (The Zemanta screenshot from Flickr in this post was inserted with just that one click.)
In addition, Zemanta looks for words/phrases it's familiar with, and makes it easy to link those words to URLs it knows about. The phrases appear immediately below the post editor in Blogger, and by clicking on them you automatically create the links Zemanta recommends. No more highlighting text, clicking "Link", pasting the URL - just click the words you want linked, and Zemanta handles the creation of the link - to webpages, maps, videos or pictures.
Blogger Labels are easier to use with Zemanta, too: Zemanta automatically suggests labels for your based on the text of your post, and creates the labels for you if you like. Finally, "Latest Update" gives you a list of blog posts from other blogs writing about similar topics. It's a great way to discover sites talking about similar topics, and if you'd like to point your readers to those articles for further reading, clicking on them in the sidebar inserts them as "Related reading" links at the bottom of your post (see below).
Source: BloggerBuzz
4:34 PM | Labels: Blogging | 0 Comments
Yahoo 360 Closes on July 13 2009
Yahoo! 360° is a personal communication portal operated by Yahoo!. It is similar to other social networking sites and while text on the site still describes it as being in beta testing, in fact development has ended and the site is no longer actively supported. Long after support ended, the promised replacement social network site has never materialized.
Users can create personal web sites, share photos from Yahoo! Photos, maintain blogs, lists of local reviews, supply profile information, and see which friends are currently online. 360° also, by default, features a 'friends updates' section, under which each friend's latest update is summarized (e.g. blog posts, updates lists, new photostream etc.).
In May 2009 Yahoo! announced that Yahoo! 360° service will be officially closed on July 13, 2009 as Yahoo! developers aimed to "focus their efforts on the new profile on Yahoo".[1] Users are given options to move their Yahoo! 360° information and blog to the new profile before this deadline.
Yahoo 360
4:28 PM | Labels: Internet, Yahoo | 0 Comments
Searches flood Google about the death of the Pop King

The spike in searches related to Michael Jackson was so big that Google News initially mistook it for an automated attack. As a result, for about 25 minutes yesterday, when some people searched Google News they saw a "We're sorry" page before finding the articles they were looking for.
Michael Jackson led an amazing and controversial life in the public eye. Many of us have a "Michael Jackson story." Mine is that he actually taught me how to moonwalk — thanks to many an hour I spent in front of the television trying to mimic his performances. Regardless of your story or personal opinions about this astounding performer, global interest in the King of Pop is undeniable.
4:14 PM | Labels: News | 0 Comments
Giveaway: Kaspersky Internet Security 2009 , 5 Licenses
As a measure to increase the popularity of my blog, I have decided to give away 5 licenses of Kaspersky Internet Security 2009.
Download Kaspersky Internet Security 2009 and follow the below guidelines.
All you have to do is :
1. Subscribe to my newsletter.
2. Subscribe to my Google SMS Channel.
4. Post a comment in my blog for most of the posts posted between 26 June 2009 and 25 July 2009.
5. I'll select the lucky winners using a lot method.
6. And I'll send the license keys to the winners' email address
P.S : The version of the software 2009 may be changed to 2010 depending upon availability.
7:28 PM | Labels: Antivirus, Kaspersky | 0 Comments
How to be a Good Blogger
After successfully running a blog for over a month, I have come up with some tips for the wannabe bloggers and the new ones out there. I am no authority on blogging and these tips are based on just my experience.
1. Try to post an article atleast 5 days a week.
2. To get an idea about what to post, visit other blogs which have the same niche as your blog.
3. Post comments in other blogs and also post a link to your blog on the bottom of the comment.
4. Use social bookmarking sites like Digg, Delicious, Technorati to make your blog popular.
5. Create a channel for your blog at Twitter and update it as you update your blog.
6. Do not post more than 2 posts per day. I dont know why, but it will seem heavy on the reader's eyes.
7. In case, you copy some information from another blog, give the owner of the information credit, by posting the source of the information at the end of the post.
8. Use traffic analysis services like Google Analytics, Statcounter, Sitemeter, Histats to monitor the traffic and sources of your blog. Most of these services give a reasonable amount of data about your blog's traffic for free
9. Do not subscribe to any sites that offer link exchanges on a category basis. This may have an effect on your blog in Google search.
10. In case you need to exchange links, contact the administrator of the blog you wish to exchange with and come up with a good reason why he/she should exchange links with you.
I am sure the above tips would help you. Use the comments options if you think any of the above tips are incorrect or if you have any more tips that will be useful.
6:51 PM | Labels: Blogging, Internet | 0 Comments
Microsoft Security Essentials Reviewed
Microsoft Security Essentials released by Microsoft a few days ago has nothing special about it. It has the usual Scan options.
It has a real time protection which alerts you when viruses, spyware or other potentially unwanted software attempts to install itself or run on your computer.
However, it has good detection capabilites. When it detects a virus, it gives you the description about the virus without connecting to the internet, unlike Kaspersky Antivirus which connects to its Virus database to access the information about the virus.
It has an option for how to react with threats, Microsoft SpyNet.
Microsoft Spynet is the online community that helps you choose how to respond to potential threats. The community also helps stop the spread of new malicious software infections.


Microsoft Security Essentials just detects the threats very well, but for reliability, we have to see in the long run. Although it doesn't have any special features, it does a good job on its own.
6:30 PM | Labels: Antivirus, Microsoft, Security, Windows | 0 Comments
Microsoft Security Essentials Beta released
Previous: Leaked: Microsoft Security Essentials
Microsoft officially released its antivirus product "Microsoft Security Essentials" beta version. It was previously named "Morro" after a beach in Brazil. The latest definitions for Microsoft Security Essentials are also available on the site.
Minimum system requirements for Microsoft Security Essentials Beta
* Operating System: Windows XP (Service Pack 2 or Service Pack 3); Windows Vista; Windows 7 (Beta or Release Candidate)
* For Windows XP, a Personal Computer with a:
o CPU with clock speed of 500 MHz or higher
o Memory: 256 MB RAM or higher
* For Windows Vista and Windows 7, a Personal Computer with a:
o CPU with clock speed of 1.0 GHz or higher
o Memory: 1 GB RAM or higher
* VGA (Display): 800 x 600 or higher
* Storage: 140 MB of available hard-disk space
* An Internet connection is required for installation and to download the latest virus and spyware definitions for Microsoft Microsoft Security Essentials.
* Internet Browser:
o Windows Internet Explorer 6.0 or later
o Mozilla Firefox 2.0 or later
For information visit
http://microsoft.com/security_Essentials
Download here
7:40 PM | Labels: Antivirus, Microsoft, Security | 0 Comments
Protect your data from being stolen
Firewalls and antivirus software are no defense against acts of data theft and corruption from within your organization at local endpoints. You don't have to be an administrator to connect a small digital camera, MP3 player, or flash memory stick to the USB and begin uploading or downloading whatever you want. If you are a system administrator, you know you can't manage such device-level activity via Group Policy.
Using endpoint device security solution called DeviceLock®, network administrators can lock out unauthorized users from USB and FireWire devices, WiFi and Bluetooth adapters, CD-Rom and floppy drives, serial and parallel ports, PDAs and smartphones, local and network printers and many other plug-and-play devices. Once DeviceLock® is installed, administrators can control access to any device, depending on the time of day and day of the week.
For enterprises standardized on software and hardware-based encryption solutions like PGP® Whole Disk Encryption, TrueCrypt and Lexar® SAFE PSD S1100 USB drives, DeviceLock® allows administrators to centrally define and remotely control the encryption policies their employees must follow when using removable devices for storing and retrieving corporate data. For example, certain employees or their groups can be allowed to write to and read from only specifically encrypted USB flash drives, while other users of the corporate network can be permitted to "read only" from non-encrypted removable storage devices but not write to them.
The USB white list allows you to authorize only specific devices that will not be locked regardless of any other settings. The intention is to allow special devices (e.g. smart card readers) but lock all other devices. Media White List feature allows you to authorize access to specific DVD/CD-ROM disks, uniquely identified by data signature, even when DeviceLock® has otherwise blocked the DVD/CD-ROM drive. A convenience when DVD/CD-ROM disks are routinely used for the distribution of new software or instruction manuals, Media White Listing can also specify allowed users and groups, so that only authorized users are able to access the contents of the DVD or CD-ROM.
The DeviceLock®'s optional data shadowing capability significantly enhances the corporate IT auditor’s ability to ensure that sensitive information has not left the premises on removable media. It captures full copies of files that are copied to authorized removable devices, Windows Mobile and Palm OS-based PDAs and smartphones, burned to CD/DVD or even printed by authorized end users. Shadow copies are stored on a centralized component of an existing server and any existing ODBC-compliant SQL infrastructure of the customer’s choosing.
DeviceLock® Enterprise Server can monitor remote computers in real-time, checking DeviceLock® Service status (running or not), policy consistency and integrity. The detailed information is written to the Monitoring log. Also, it is possible to define a master policy that can be automatically applied across selected remote computers in the event that their current policies are suspected to be out-of-date or damaged.
DeviceLock® allows you to generate a report concerning the permissions that have been set. You can see which users are assigned for what device and what devices are on the USB white list on all the computers across your network.
DeviceLock® provides a level of precision control over device resources unavailable via Windows Group Policy - and it does so with an interface that is seamlessly integrated into the Windows Group Policy Editor. As such, it’s easier to implement and manage across a large number of workstations.
For more information, visit www.devicelock.com
Download
7:10 PM | Labels: Security, Software | 0 Comments
Send anonymous email
You can send emails to anyone without disclosing your identity. It may be helpful when you want to play a trick on your friends.
Disclaimer: This is for EDUCATIONAL purposes only.
Now let me explain the procedure.
1. Go to Youmail.ws
2. Just enter an email id or anything in the format
name@something.something
in the Sender
3. Enter the address you want to send to in the Sendto
4. Now, enter the subject and the body of the email and press Send E-mail.
You cannot send attachments using this website. You can only send text messages.
Have fun!!!
Youmail
7:47 PM | Labels: Internet | 2 Comments
Proxy software for Windows and Mac
Proxifier is a program that allows network applications that do not support working through proxy servers operate through a HTTP or SOCKS proxy server or a chain of proxy servers. Proxifier will provide you with added privacy in all your Internet activities. An example is sending and receiving email through a proxy server or by chaining multiple proxy servers together. Proxifier supports all mail clients while allowing you to remain anonymous.
There are many network applications that do not support working through proxy servers and thus cannot be used behind a LAN or firewall(s). These can compromise corporate privacy and lead you to many other restrictions. Proxifier solves all of these problems and gives you the opportunity to work with your favorite software without any restrictions. Additionally, it lets you gain extra control over network security, create a proxy tunnel and add more power to network functionality. With Proxifier you can work with any Internet client (browsers, FTP, IRC, BitTorrent, messengers, telnet, SSH, video/audio, games...) through a network that is separated from Internet by a firewall (only one open port is required for a proxy tunnel to bypass firewall).
Portable Edition has most of Proxifier features while providing you with unique opportunities:
The software is a trial version for 31 days.
Proxifier allows you to: Proxifier Portable Edition:
Download - Windows
Download-MacOSX
Download-Portable Edition
7:19 PM | Labels: Mac, Proxy, Software, Windows | 0 Comments
How to Backup Internet Explorer and Firefox Bookmarks, Settings, and History
MozBackup is a simple utility for creating backups of Mozilla Firefox, Mozilla Thunderbird, Mozilla Sunbird, Flock, SeaMonkey, Mozilla Suite, Spicebird, Songbird and Netscape profiles. It allows you to backup and restore bookmarks, mail, contacts, history, extensions, cache etc. It is an easy way to backup the above browsers. MozBackup is compatible with:


This program is a freeware and works on Windows 98/ME/NT/2000/XP/2003/Vista.
Download
6:27 PM | Labels: Firefox, Internet, Internet Explorer, Software | 0 Comments
Customize Firefox to your memory needs
Limit RAM usage:
If Firefox takes up too much memory on your computer, you can limit the amount of RAM it is allowed to us.
1. Go to about:config by typing about:config in the address bar.
2. Select "browser.cache.disk.capacity". It is set to 50000, but you can lower it, depending on how much memory you have. Try 15000 if you have between 512MB and 1GB ram.
Reduce RAM usage further for when Firefox is minimized:
This setting will move Firefox to your hard drive when you minimize it, taking up much less memory. And there is no noticeable difference in speed when you restore Firefox, so it’s definitely worth a go.
1. Go to about:config
2. Right-click anywhere and select New-> Boolean.
3. Name it "config.trim_on_minimize" and set it to TRUE. You have to restart Firefox for these settings to take effect.
4:00 PM | Labels: Firefox | 0 Comments
Trace the sender of an email using IP Address
Hi Readers, I will show you how to trace an email sender from the email header. Every email comes with information attached to it about its history. This information is called the header. A header will look somewhat similar to the below:
MIME-Version: 1.0
Received: from rwcrmhc11.comcast.net ([204.127.198.35]) by mc7-f12.hotmail.com with Microsoft SMTPSVC(5.0.2195.6713); Tue, 25 Nov 2003 19:56:18 -0800
Received: from pavilion (pcp03530790pcs.mnhwkn01.nj.comcast.net[68.37.24.150]) by comcast.net (rwcrmhc11) with SMTP id <20031126034457013001nk6pe>; Wed, 26 Nov 2003 03:44:57 +0000
X-Message-Info: JGTYoYF78jGkTvdOiviUvHyY85nt7iLD
Message-ID: <000801c3b3cf$a92237a0$96182544@mnhwkn01.nj.comcast.net>
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2800.1106
Disposition-Notification-To: "Leona"
X-MimeOLE: Produced By Microsoft MimeOLE V6.00.2800.1106
Return-Path: leona6256@comcast.net
X-OriginalArrivalTime: 26 Nov 2003 03:56:18.0897 (UTC) FILETIME=[3F5AFC10:01C3B3D1]
First, let me tell you how to view the header file of an email.
Gmail
1. Login to Gmail.
2. Open the message you'd like to view headers for.
3. Click the down arrow next to Reply, at the top-right of the message pane.
4. Select Show original. The full headers will appear in a new window.
Hotmail
1. Log in to your Hotmail account.
2. Click Options next to the tabs.
3. Select Mail from the left-side menu.
4. Click Mail Display Settings.
5. Under Message Headers, select Advanced.
6. Click OK.
The full headers for all of your messages will now be available. Return to your inbox, and open the message you'd like to view headers for.
Yahoo! Mail
1. Log in to your Yahoo! Mail account.
2. Open the message you'd like to view headers for.
3. Click Full Headers at the top of your message. The full headers will appear above the message text.
Now, I will explain what each title in the header file means:
Message ID:
It is used to identify the system from which the the message has originated (i.e. from the system the sender has logged in). However, this is too easy to forge, and is consequently not reliable.
X- headers are user defined headers. They are inserted by email client programs or applications that use email. Here from the X- headers inserted into the email by the email client it is clear that the sender has used Microsoft Outlook Express 6.00.2800.1106 to send this email.
X-Priority: 3
X-MSMail-Priority: Normal
X-Mailer: Microsoft Outlook Express 6.00.2800.1106
MIME-Version:
MIME stands for Multipurpose Internet Mail Extension. It tells the recipient what types of attachments are included in email. It is a format that allows people to send attachments that do not contain Standard English Words, but rather graphics, sounds, and e-mails written with other characters. The Mime-Version field merely confirms that the version of MIME used corresponds to the standard version (which is currently 1.0).
From:
From is useless in tracing an e-mail. It consists of the email of the sender but this can be obviously be a fake. One can use any fake-mailer to fake the sender's name.
Content-Type:
This line tells the receiving e-mail client exactly what MIME type or types are included in the e-mail message. If the Content–Type is text/plain; charset="us-ascii" just tells us that the message contains a regular text message that uses English characters. ASCII is the American Standard Code for Information Interchange and is the system used to convert numbers to English characters.
Return-Path:
It is the address to which your return e-mail will be sent. Different e-mail programs use other variations of Return-Path:. These might include Return-Errors-To: or Reply-To etc.
Received:
This field is the key to find out the source of any e-mail. Like a regular letter, e-mails gets postmarked with information that tells where it has been. However, unlike a regular letter, an e-mail might get "postmarked" any number of times as it makes its way from its source through a number of mail transfer agents (MTAs). The MTAs are responsible for properly routing messages to their destination.
The header is splitted and the two received headers are given below.
Received Header 1: 204.127.198.35 - Tue, 25 Nov 2003 19:56:18 -0800
from rwcrmhc11.comcast.net ([204.127.198.35])
by mc7-f12.hotmail.com
with Microsoft SMTPSVC(5.0.2195.6713)
Received Header 2: 68.37.24.150 - Wed, 26 Nov 2003 03:44:57 +0000
from pavilion (pcp03530790pcs.mnhwkn01.nj.comcast.net[68.37.24.150])
by comcast.net (rwcrmhc11)
with SMTP
id <20031126034457013001nk6pe>
Note down the IP Address in the last received header, in this case it is 68.37.24.150. This is the IP Address from where the email has originated.
Tracing the owner by the IP Address
Every computers hooked on to internet is assigned with an IP address. Individual users possess a dynamic IP address when they logged on to any ISP to access internet. These IP addresses are assigned by the ISP itself. Organization usually possess static/public IP address which is stored in a database of registries.
There are three major registries covering different parts of the world. They are
http://www.arin.net/ => American Registry of Internet Numbers (ARIN) : It assigns IP addresses for the Americas and for sub Saharan Africa.
http://www.apnic.net/ => Asia Pacific Network Information Centre (APNIC) : It covers Asia
http://www.ripe.net/ => Réseaux IP Européens (RIPE NCC) : It covers Europe
Thus, to find out which organization owns a particular IP address, you can make a "WHOIS" query in the database at any of these registries. You do this by typing the IP address into the "WHOIS" box that appears on each of these websites.
"Received Header" will have the IP address of the ISP in case the users has dialed up to the ISP while sending the email. But if the user has send the email from within the corporate then the corporate public/static IP address is logged.
3:45 PM | Labels: IP Addresses | 1 Comments
Ports Used by Trojan Horses
Hi readers, I discovered some useful information about viruses and trojan horses. Viruses and Trojan Horses use ports to make use of our system resources. Ports are similar to the real ship ports, they handle data in and out of the system. They are virtual. The following is the list of ports that applications and trojan horses use to get access. Ports range from 0 to 65535.
Default ports used by some known trojan horses:
port 0 REx
port 1 (UDP) - Sockets des Troie
port 2 Death
port 5 yoyo
port 11 Skun
port 16 Skun
port 17 Skun
port 18 Skun
port 19 Skun
port 20 Amanda
port 21 ADM worm, Back Construction, Blade Runner, BlueFire, Bmail, Cattivik FTP Server, CC Invader, Dark FTP, Doly Trojan, FreddyK, Invisible FTP, KWM, MscanWorm, NerTe, NokNok, Pinochet, Ramen, Reverse Trojan, RTB 666, The Flu, WinCrash, Voyager Alpha Force
port 22 InCommand, Shaft, Skun
port 23 ADM worm, Aphex's Remote Packet Sniffer , AutoSpY, ButtMan, Fire HacKer, My Very Own trojan, Pest, RTB 666, Tiny Telnet Server - TTS, Truva Atl
port 25 Antigen, Barok, BSE, Email Password Sender , Gip, Laocoon, Magic Horse, MBT , Moscow Email trojan, Nimda, Shtirlitz, Stukach, Tapiras, WinPC
port 27 Assasin
port 28 Amanda
port 30 Agent 40421
port 31 Agent 40421, Masters Paradise, Skun
port 37 ADM worm
port 39 SubSARI
port 41 Deep Throat , Foreplay
port 44 Arctic
port 51 Fuck Lamers Backdoor
port 52 MuSka52, Skun
port 53 ADM worm, li0n, MscanWorm, MuSka52
port 54 MuSka52
port 66 AL-Bareki
port 69 BackGate Kit, Nimda, Pasana, Storm, Storm worm, Theef
port 69 (UDP) - Pasana
port 70 ADM worm
port 79 ADM worm, Firehotcker
port 80 711 trojan (Seven Eleven), AckCmd, BlueFire, Cafeini, Duddie, Executor, God Message, Intruzzo , Latinus, Lithium, MscanWorm, NerTe, Nimda, Noob, Optix Lite, Optix Pro , Power, Ramen, Remote Shell , Reverse WWW Tunnel Backdoor , RingZero, RTB 666, Scalper, Screen Cutter , Seeker, Slapper, Web Server CT , WebDownloader
port 80 (UDP) - Penrox
port 81 Asylum
port 101 Skun
port 102 Delf, Skun
port 103 Skun
port 105 NerTe
port 107 Skun
port 109 ADM worm
port 110 ADM worm
port 111 ADM worm, MscanWorm
port 113 ADM worm, Alicia, Cyn, DataSpy Network X, Dosh, Gibbon, Taskman
port 120 Skun
port 121 Attack Bot, God Message, JammerKillah
port 123 Net Controller
port 137 Chode, Nimda
port 137 (UDP) - Bugbear, Msinit, Opaserv, Qaz
port 138 Chode, Nimda
port 139 Chode, Fire HacKer, Msinit, Nimda, Opaserv, Qaz
port 143 ADM worm
port 146 Infector
port 146 (UDP) - Infector
port 166 NokNok
port 170 A-trojan
port 171 A-trojan
port 200 CyberSpy
port 201 One Windows Trojan
port 202 One Windows Trojan, Skun
port 211 One Windows Trojan
port 212 One Windows Trojan
port 221 Snape
port 222 NeuroticKat, Snape
port 230 Skun
port 231 Skun
port 232 Skun
port 285 Delf
port 299 One Windows Trojan
port 334 Backage
port 335 Nautical
port 370 NeuroticKat
port 400 Argentino
port 401 One Windows Trojan
port 402 One Windows Trojan
port 411 Backage
port 420 Breach
port 443 Slapper
port 445 Nimda
port 455 Fatal Connections
port 511 T0rn Rootkit
port 513 ADM worm
port 514 ADM worm
port 515 MscanWorm, Ramen
port 520 (UDP) - A UDP backdoor
port 555 711 trojan (Seven Eleven), Phase Zero, Phase-0
port 564 Oracle
port 589 Assasin
port 600 SweetHeart
port 623 RTB 666
port 635 ADM worm
port 650 Assasin
port 661 NokNok
port 666 Attack FTP, Back Construction, BLA trojan, NokNok, Reverse Trojan, Shadow Phyre, Unicorn, yoyo
port 667 NokNok, SniperNet
port 668 Unicorn
port 669 DP trojan , SniperNet
port 680 RTB 666
port 692 GayOL
port 700 REx
port 777 Undetected
port 798 Oracle
port 808 WinHole
port 831 NeuroticKat
port 901 Net-Devil, Pest
port 902 Net-Devil, Pest
port 903 Net-Devil
port 911 Dark Shadow, Dark Shadow
port 956 Crat Pro
port 991 Snape
port 992 Snape
port 999 Deep Throat , Foreplay
port 1000 Der Späher / Der Spaeher, Direct Connection, GOTHIC Intruder , Theef
port 1001 Der Späher / Der Spaeher, GOTHIC Intruder , Lula, One Windows Trojan, Theef
port 1005 Pest, Theef
port 1008 AutoSpY, li0n
port 1010 Doly Trojan
port 1011 Doly Trojan
port 1012 Doly Trojan
port 1015 Doly Trojan
port 1016 Doly Trojan
port 1020 Vampire
port 1024 Latinus, Lithium, NetSpy, Ptakks
port 1025 AcidkoR, BDDT, DataSpy Network X, Fraggle Rock , KiLo, MuSka52, NetSpy, Optix Pro , Paltalk, Ptakks, Real 2000, Remote Anything, Remote Explorer Y2K, Remote Storm, RemoteNC
port 1025 (UDP) - KiLo, Optix Pro , Ptakks, Real 2000, Remote Anything, Remote Explorer Y2K, Remote Storm, Yajing
port 1026 BDDT, Dark IRC, DataSpy Network X, Delta Remote Access , Dosh, Duddie, IRC Contact, Remote Explorer 2000, RUX The TIc.K
port 1026 (UDP) - Remote Explorer 2000
port 1027 Clandestine, DataSpy Network X, KiLo, UandMe
port 1028 DataSpy Network X, Dosh, Gibbon, KiLo, KWM, Litmus, Paltalk, SubSARI
port 1028 (UDP) - KiLo, SubSARI
port 1029 Clandestine, KWM, Litmus, SubSARI
port 1029 (UDP) - SubSARI
port 1030 Gibbon, KWM
port 1031 KWM, Little Witch, Xanadu, Xot
port 1031 (UDP) - Xot
port 1032 Akosch4, Dosh, KWM
port 1032 (UDP) - Akosch4
port 1033 Dosh, KWM, Little Witch, Net Advance
port 1034 KWM
port 1035 Dosh, KWM, RemoteNC, Truva Atl
port 1036 KWM
port 1037 Arctic , Dosh, KWM, MoSucker
port 1039 Dosh
port 1041 Dosh, RemoteNC
port 1042 BLA trojan
port 1042 (UDP) - BLA trojan
port 1043 Dosh
port 1044 Ptakks
port 1044 (UDP) - Ptakks
port 1047 RemoteNC
port 1049 Delf, The Hobbit Daemon
port 1052 Fire HacKer, Slapper, The Hobbit Daemon
port 1053 The Thief
port 1054 AckCmd, RemoteNC
port 1080 SubSeven 2.2, WinHole
port 1081 WinHole
port 1082 WinHole
port 1083 WinHole
port 1092 Hvl RAT
port 1095 Blood Fest Evolution, Hvl RAT, Remote Administration Tool - RAT
port 1097 Blood Fest Evolution, Hvl RAT, Remote Administration Tool - RAT
port 1098 Blood Fest Evolution, Hvl RAT, Remote Administration Tool - RAT
port 1099 Blood Fest Evolution, Hvl RAT, Remote Administration Tool - RAT
port 1104 (UDP) - RexxRave
port 1111 Daodan, Ultors Trojan
port 1111 (UDP) - Daodan
port 1115 Lurker, Protoss
port 1116 Lurker
port 1116 (UDP) - Lurker
port 1122 Last 2000, Singularity
port 1122 (UDP) - Last 2000, Singularity
port 1133 SweetHeart
port 1150 Orion
port 1151 Orion
port 1160 BlackRat
port 1166 CrazzyNet
port 1167 CrazzyNet
port 1170 Psyber Stream Server , Voice
port 1180 Unin68
port 1183 Cyn, SweetHeart
port 1183 (UDP) - Cyn, SweetHeart
port 1200 (UDP) - NoBackO
port 1201 (UDP) - NoBackO
port 1207 SoftWAR
port 1208 Infector
port 1212 Kaos
port 1215 Force
port 1218 Force
port 1219 Force
port 1221 Fuck Lamers Backdoor
port 1222 Fuck Lamers Backdoor
port 1234 KiLo, Ultors Trojan
port 1243 BackDoor-G, SubSeven , Tiles
port 1245 VooDoo Doll
port 1255 Scarab
port 1256 Project nEXT, RexxRave
port 1272 The Matrix
port 1313 NETrojan
port 1314 Daodan
port 1349 BO dll
port 1369 SubSeven 2.2
port 1386 Dagger
port 1415 Last 2000, Singularity
port 1433 Voyager Alpha Force
port 1441 Remote Storm
port 1492 FTP99CMP
port 1524 Trinoo
port 1560 Big Gluck, Duddie
port 1561 (UDP) - MuSka52
port 1600 Direct Connection
port 1601 Direct Connection
port 1602 Direct Connection
port 1703 Exploiter
port 1711 yoyo
port 1772 NetControle
port 1772 (UDP) - NetControle
port 1777 Scarab
port 1826 Glacier
port 1833 TCC
port 1834 TCC
port 1835 TCC
port 1836 TCC
port 1837 TCC
port 1905 Delta Remote Access
port 1911 Arctic
port 1966 Fake FTP
port 1967 For Your Eyes Only , WM FTP Server
port 1978 (UDP) - Slapper
port 1981 Bowl, Shockrave
port 1983 Q-taz
port 1984 Intruzzo , Q-taz
port 1985 Black Diver, Q-taz
port 1985 (UDP) - Black Diver
port 1986 Akosch4
port 1991 PitFall
port 1999 Back Door, SubSeven , TransScout
port 2000 A-trojan, Der Späher / Der Spaeher, Fear, Force, GOTHIC Intruder , Last 2000, Real 2000, Remote Explorer 2000, Remote Explorer Y2K, Senna Spy Trojan Generator, Singularity
port 2000 (UDP) - GOTHIC Intruder , Real 2000, Remote Explorer 2000, Remote Explorer Y2K
port 2001 Der Späher / Der Spaeher, Duddie, Glacier, Protoss, Senna Spy Trojan Generator, Singularity, Trojan Cow
port 2001 (UDP) - Scalper
port 2002 Duddie, Senna Spy Trojan Generator, Sensive
port 2002 (UDP) - Slapper
port 2004 Duddie
port 2005 Duddie
port 2023 Ripper Pro
port 2060 Protoss
port 2080 WinHole
port 2101 SweetHeart
port 2115 Bugs
port 2130 (UDP) - Mini BackLash
port 2140 The Invasor
port 2140 (UDP) - Deep Throat , Foreplay , The Invasor
port 2149 Deep Throat
port 2150 R0xr4t
port 2156 Oracle
port 2222 SweetHeart, Way
port 2222 (UDP) - SweetHeart, Way
port 2281 Nautical
port 2283 Hvl RAT
port 2300 Storm
port 2311 Studio 54
port 2330 IRC Contact
port 2331 IRC Contact
port 2332 IRC Contact, Silent Spy
port 2333 IRC Contact
port 2334 IRC Contact, Power
port 2335 IRC Contact
port 2336 IRC Contact
port 2337 IRC Contact, The Hobbit Daemon
port 2338 IRC Contact
port 2339 IRC Contact, Voice Spy
port 2339 (UDP) - Voice Spy
port 2343 Asylum
port 2345 Doly Trojan
port 2407 yoyo
port 2418 Intruzzo
port 2555 li0n, T0rn Rootkit
port 2565 Striker trojan
port 2583 WinCrash
port 2589 Dagger
port 2600 Digital RootBeer
port 2702 Black Diver
port 2702 (UDP) - Black Diver
port 2772 SubSeven
port 2773 SubSeven , SubSeven 2.1 Gold
port 2774 SubSeven , SubSeven 2.1 Gold
port 2800 Theef
port 2929 Konik
port 2983 Breach
port 2989 (UDP) - Remote Administration Tool - RAT
port 3000 InetSpy, Remote Shut, Theef
port 3006 Clandestine
port 3024 WinCrash
port 3031 MicroSpy
port 3119 Delta Remote Access
port 3128 Reverse WWW Tunnel Backdoor , RingZero
port 3129 Masters Paradise
port 3131 SubSARI
port 3150 Deep Throat , The Invasor, The Invasor
port 3150 (UDP) - Deep Throat , Foreplay , Mini BackLash
port 3215 XHX
port 3215 (UDP) - XHX
port 3292 Xposure
port 3295 Xposure
port 3333 Daodan
port 3333 (UDP) - Daodan
port 3410 Optix Pro
port 3417 Xposure
port 3418 Xposure
port 3456 Fear, Force, Terror trojan
port 3459 Eclipse 2000, Sanctuary
port 3505 AutoSpY
port 3700 Portal of Doom
port 3721 Whirlpool
port 3723 Mantis
port 3777 PsychWard
port 3791 Total Solar Eclypse
port 3800 Total Solar Eclypse
port 3801 Total Solar Eclypse
port 3945 Delta Remote Access
port 3996 Remote Anything
port 3996 (UDP) - Remote Anything
port 3997 Remote Anything
port 3999 Remote Anything
port 4000 Remote Anything, SkyDance
port 4092 WinCrash
port 4128 RedShad
port 4128 (UDP) - RedShad
port 4156 (UDP) - Slapper
port 4201 War trojan
port 4210 Netkey
port 4211 Netkey
port 4225 Silent Spy
port 4242 Virtual Hacking Machine - VHM
port 4315 Power
port 4321 BoBo
port 4414 AL-Bareki
port 4442 Oracle
port 4444 CrackDown, Oracle, Prosiak, Swift Remote
port 4445 Oracle
port 4447 Oracle
port 4449 Oracle
port 4451 Oracle
port 4488 Event Horizon
port 4567 File Nail
port 4653 Cero
port 4666 Mneah
port 4700 Theef
port 4836 Power
port 5000 Back Door Setup, Bubbel, Ra1d, Sockets des Troie
port 5001 Back Door Setup, Sockets des Troie
port 5002 Shaft
port 5005 Aladino
port 5011 Peanut Brittle
port 5025 WM Remote KeyLogger
port 5031 Net Metropolitan
port 5032 Net Metropolitan
port 5050 R0xr4t
port 5135 Bmail
port 5150 Pizza
port 5151 Optix Lite
port 5152 Laphex
port 5155 Oracle
port 5221 NOSecure
port 5250 Pizza
port 5321 Firehotcker
port 5333 Backage
port 5350 Pizza
port 5377 Iani
port 5400 Back Construction, Blade Runner, Digital Spy
port 5401 Back Construction, Blade Runner, Digital Spy , Mneah
port 5402 Back Construction, Blade Runner, Digital Spy , Mneah
port 5418 DarkSky
port 5419 DarkSky
port 5419 (UDP) - DarkSky
port 5430 Net Advance
port 5450 Pizza
port 5503 Remote Shell
port 5534 The Flu
port 5550 Pizza
port 5555 Daodan, NoXcape
port 5555 (UDP) - Daodan
port 5556 BO Facil
port 5557 BO Facil
port 5569 Robo-Hack
port 5650 Pizza
port 5669 SpArTa
port 5679 Nautical
port 5695 Assasin
port 5696 Assasin
port 5697 Assasin
port 5742 WinCrash
port 5802 Y3K RAT
port 5873 SubSeven 2.2
port 5880 Y3K RAT
port 5882 Y3K RAT
port 5882 (UDP) - Y3K RAT
port 5888 Y3K RAT
port 5888 (UDP) - Y3K RAT
port 5889 Y3K RAT
port 5933 NOSecure
port 6000 Aladino, NetBus , The Thing
port 6006 Bad Blood
port 6267 DarkSky
port 6400 The Thing
port 6521 Oracle
port 6526 Glacier
port 6556 AutoSpY
port 6661 Weia-Meia
port 6666 AL-Bareki, KiLo, SpArTa
port 6666 (UDP) - KiLo
port 6667 Acropolis, BlackRat, Dark FTP, Dark IRC, DataSpy Network X, Gunsan, InCommand, Kaitex, KiLo, Laocoon, Net-Devil, Reverse Trojan, ScheduleAgent, SlackBot, SubSeven , Subseven 2.1.4 DefCon 8, Trinity, Y3K RAT, yoyo
port 6667 (UDP) - KiLo
port 6669 Host Control, Vampire, Voyager Alpha Force
port 6670 BackWeb Server, Deep Throat , Foreplay , WinNuke eXtreame
port 6697 Force
port 6711 BackDoor-G, Duddie, KiLo, Little Witch, Netkey, Spadeace, SubSARI, SubSeven , SweetHeart, UandMe, Way, VP Killer
port 6712 Funny trojan, KiLo, Spadeace, SubSeven
port 6713 KiLo, SubSeven
port 6714 KiLo
port 6715 KiLo
port 6718 KiLo
port 6723 Mstream
port 6766 KiLo
port 6766 (UDP) - KiLo
port 6767 KiLo, Pasana, UandMe
port 6767 (UDP) - KiLo, UandMe
port 6771 Deep Throat , Foreplay
port 6776 2000 Cracks, BackDoor-G, SubSeven , VP Killer
port 6838 (UDP) - Mstream
port 6891 Force
port 6912 Shit Heep
port 6969 2000 Cracks, BlitzNet, Dark IRC, GateCrasher, Kid Terror, Laphex, Net Controller, SpArTa, Vagr Nocker
port 6970 GateCrasher
port 7000 Aladino, Gunsan, Remote Grab, SubSeven , SubSeven 2.1 Gold, Theef
port 7001 Freak88, Freak2k
port 7007 Silent Spy
port 7020 Basic Hell
port 7030 Basic Hell
port 7119 Massaker
port 7215 SubSeven , SubSeven 2.1 Gold
port 7274 AutoSpY
port 7290 NOSecure
port 7291 NOSecure
port 7300 NetSpy
port 7301 NetSpy
port 7306 NetSpy
port 7307 NetSpy, Remote Process Monitor
port 7308 NetSpy, X Spy
port 7312 Yajing
port 7410 Phoenix II
port 7424 Host Control
port 7424 (UDP) - Host Control
port 7597 Qaz
port 7626 Glacier
port 7648 XHX
port 7673 Neoturk
port 7676 Neoturk
port 7677 Neoturk
port 7718 Glacier
port 7722 KiLo
port 7777 God Message
port 7788 Last 2000, Last 2000, Singularity
port 7788 (UDP) - Singularity
port 7789 Back Door Setup
port 7800 Paltalk
port 7826 Oblivion
port 7850 Paltalk
port 7878 Paltalk
port 7879 Paltalk
port 7979 Vagr Nocker
port 7983 (UDP) - Mstream
port 8011 Way
port 8012 Ptakks
port 8012 (UDP) - Ptakks
port 8080 Reverse WWW Tunnel Backdoor , RingZero, Screen Cutter
port 8090 Aphex's Remote Packet Sniffer
port 8090 (UDP) - Aphex's Remote Packet Sniffer
port 8097 Kryptonic Ghost Command Pro
port 8100 Back streets
port 8110 DLP
port 8111 DLP
port 8127 9_119, Chonker
port 8127 (UDP) - 9_119, Chonker
port 8130 9_119, Chonker, DLP
port 8131 DLP
port 8301 DLP
port 8302 DLP
port 8311 SweetHeart
port 8322 DLP
port 8329 DLP
port 8488 (UDP) - KiLo
port 8489 KiLo
port 8489 (UDP) - KiLo
port 8685 Unin68
port 8732 Kryptonic Ghost Command Pro
port 8734 AutoSpY
port 8787 Back Orifice 2000
port 8811 Fear
port 8812 FraggleRock Lite
port 8821 Alicia
port 8848 Whirlpool
port 8864 Whirlpool
port 8888 Dark IRC
port 9000 Netministrator
port 9090 Aphex's Remote Packet Sniffer
port 9117 Massaker
port 9148 Nautical
port 9301 DLP
port 9325 (UDP) - Mstream
port 9329 DLP
port 9400 InCommand
port 9401 InCommand
port 9536 Lula
port 9561 Crat Pro
port 9563 Crat Pro
port 9870 Remote Computer Control Center
port 9872 Portal of Doom
port 9873 Portal of Doom
port 9874 Portal of Doom
port 9875 Portal of Doom
port 9876 Rux
port 9877 Small Big Brother
port 9878 Small Big Brother, TransScout
port 9879 Small Big Brother
port 9919 Kryptonic Ghost Command Pro
port 9999 BlitzNet, Oracle, Spadeace
port 10000 Oracle, TCP Door, XHX
port 10000 (UDP) - XHX
port 10001 DTr, Lula
port 10002 Lula
port 10003 Lula
port 10008 li0n
port 10012 Amanda
port 10013 Amanda
port 10067 Portal of Doom
port 10067 (UDP) - Portal of Doom
port 10084 Syphillis
port 10084 (UDP) - Syphillis
port 10085 Syphillis
port 10086 Syphillis
port 10100 Control Total, GiFt trojan, Scalper
port 10100 (UDP) - Slapper
port 10167 Portal of Doom
port 10167 (UDP) - Portal of Doom
port 10498 (UDP) - Mstream
port 10520 Acid Shivers
port 10528 Host Control
port 10607 Coma
port 10666 (UDP) - Ambush
port 10887 BDDT
port 10889 BDDT
port 11000 DataRape, Senna Spy Trojan Generator
port 11011 Amanda
port 11050 Host Control
port 11051 Host Control
port 11111 Breach
port 11223 Progenic trojan, Secret Agent
port 11225 Cyn
port 11225 (UDP) - Cyn
port 11660 Back streets
port 11718 Kryptonic Ghost Command Pro
port 11831 DarkFace, DataRape, Latinus, Pest, Vagr Nocker
port 11977 Cool Remote Control
port 11978 Cool Remote Control
port 11980 Cool Remote Control
port 12000 Reverse Trojan
port 12310 PreCursor
port 12321 Protoss
port 12321 (UDP) - Protoss
port 12345 Ashley, BlueIce 2000, Mypic , NetBus , Pie Bill Gates, Q-taz , Sensive, Snape, Vagr Nocker, ValvNet , Whack Job
port 12345 (UDP) - BlueIce 2000
port 12346 NetBus
port 12348 BioNet
port 12349 BioNet, The Saint
port 12361 Whack-a-mole
port 12362 Whack-a-mole
port 12363 Whack-a-mole
port 12623 ButtMan
port 12623 (UDP) - ButtMan, DUN Control
port 12624 ButtMan, Power
port 12631 Whack Job
port 12684 Power
port 12754 Mstream
port 12904 Rocks
port 13000 Senna Spy Trojan Generator, Senna Spy Trojan Generator
port 13013 PsychWard
port 13014 PsychWard
port 13028 Back streets
port 13079 Kryptonic Ghost Command Pro
port 13370 SpArTa
port 13371 Optix Pro
port 13500 Theef
port 13753 Anal FTP
port 14194 CyberSpy
port 14285 Laocoon
port 14286 Laocoon
port 14287 Laocoon
port 14500 PC Invader
port 14501 PC Invader
port 14502 PC Invader
port 14503 PC Invader
port 15000 In Route to the Hell, R0xr4t
port 15092 Host Control
port 15104 Mstream
port 15206 KiLo
port 15207 KiLo
port 15210 (UDP) - UDP remote shell backdoor server
port 15382 SubZero
port 15432 Cyn
port 15485 KiLo
port 15486 KiLo
port 15486 (UDP) - KiLo
port 15500 In Route to the Hell
port 15512 Iani
port 15551 In Route to the Hell
port 15695 Kryptonic Ghost Command Pro
port 15845 (UDP) - KiLo
port 15852 Kryptonic Ghost Command Pro
port 16057 MoonPie
port 16484 MoSucker
port 16514 KiLo
port 16514 (UDP) - KiLo
port 16515 KiLo
port 16515 (UDP) - KiLo
port 16523 Back streets
port 16660 Stacheldraht
port 16712 KiLo
port 16761 Kryptonic Ghost Command Pro
port 16959 SubSeven , Subseven 2.1.4 DefCon 8
port 17166 Mosaic
port 17449 Kid Terror
port 17499 CrazzyNet
port 17500 CrazzyNet
port 17569 Infector
port 17593 AudioDoor
port 17777 Nephron
port 18753 (UDP) - Shaft
port 19191 BlueFire
port 19216 BackGate Kit
port 20000 Millenium, PSYcho Files, XHX
port 20001 Insect, Millenium, PSYcho Files
port 20002 AcidkoR, PSYcho Files
port 20005 MoSucker
port 20023 VP Killer
port 20034 NetBus 2.0 Pro, NetBus 2.0 Pro Hidden, Whack Job
port 20331 BLA trojan
port 20432 Shaft
port 20433 (UDP) - Shaft
port 21212 Sensive
port 21544 GirlFriend, Kid Terror
port 21554 Exploiter, FreddyK, Kid Terror, Schwindler, Sensive, Winsp00fer
port 21579 Breach
port 21957 Latinus
port 22115 Cyn
port 22222 Donald Dick, G.R.O.B., Prosiak, Ruler, RUX The TIc.K
port 22223 RUX The TIc.K
port 22456 Clandestine
port 22554 Schwindler
port 22783 Intruzzo
port 22784 Intruzzo
port 22785 Intruzzo
port 23000 Storm worm
port 23001 Storm worm
port 23005 NetTrash, Oxon
port 23006 NetTrash, Oxon
port 23023 Logged
port 23032 Amanda
port 23321 Konik
port 23432 Asylum
port 23456 Clandestine, Evil FTP, Vagr Nocker, Whack Job
port 23476 Donald Dick
port 23476 (UDP) - Donald Dick
port 23477 Donald Dick
port 23777 InetSpy
port 24000 Infector
port 24289 Latinus
port 25002 MOTD
port 25002 (UDP) - MOTD
port 25123 Goy'Z TroJan
port 25555 FreddyK
port 25685 MoonPie
port 25686 DarkFace, MoonPie
port 25799 FreddyK
port 25885 MOTD
port 25982 DarkFace, MoonPie
port 26274 (UDP) - Delta Source
port 26681 Voice Spy
port 27160 MoonPie
port 27184 Alvgus trojan 2000
port 27184 (UDP) - Alvgus trojan 2000
port 27373 Charge
port 27374 Bad Blood, Fake SubSeven, li0n, Ramen, Seeker, SubSeven , SubSeven 2.1 Gold, Subseven 2.1.4 DefCon 8, SubSeven 2.2, SubSeven Muie, The Saint
port 27379 Optix Lite
port 27444 (UDP) - Trinoo
port 27573 SubSeven
port 27665 Trinoo
port 28218 Oracle
port 28431 Hack´a´Tack
port 28678 Exploiter
port 29104 NETrojan, NetTrojan
port 29292 BackGate Kit
port 29559 AntiLamer BackDoor , DarkFace, DataRape, Ducktoy, Latinus, Pest, Vagr Nocker
port 29589 KiLo
port 29589 (UDP) - KiLo
port 29891 The Unexplained
port 29999 AntiLamer BackDoor
port 30000 DataRape, Infector
port 30001 Err0r32
port 30005 Litmus
port 30100 NetSphere
port 30101 NetSphere
port 30102 NetSphere
port 30103 NetSphere
port 30103 (UDP) - NetSphere
port 30133 NetSphere
port 30303 Sockets des Troie
port 30331 MuSka52
port 30464 Slapper
port 30700 Mantis
port 30947 Intruse
port 31320 Little Witch
port 31320 (UDP) - Little Witch
port 31335 Trinoo
port 31336 Butt Funnel
port 31337 ADM worm, Back Fire, Back Orifice (Lm), Back Orifice russian, BlitzNet, BO client, BO Facil, BO2, Freak88, Freak2k, NoBackO
port 31337 (UDP) - Back Orifice, Deep BO
port 31338 Back Orifice, Butt Funnel, NetSpy (DK)
port 31338 (UDP) - Deep BO, NetSpy (DK)
port 31339 Little Witch, NetSpy (DK), NetSpy (DK)
port 31339 (UDP) - Little Witch
port 31340 Little Witch
port 31340 (UDP) - Little Witch
port 31382 Lithium
port 31415 Lithium
port 31416 Lithium
port 31416 (UDP) - Lithium
port 31557 Xanadu
port 31745 BuschTrommel
port 31785 Hack´a´Tack
port 31787 Hack´a´Tack
port 31788 Hack´a´Tack
port 31789 Hack´a´Tack
port 31789 (UDP) - Hack´a´Tack
port 31790 Hack´a´Tack
port 31791 Hack´a´Tack
port 31791 (UDP) - Hack´a´Tack
port 31792 Hack´a´Tack
port 31887 BDDT
port 32000 BDDT
port 32001 Donald Dick
port 32100 Peanut Brittle, Project nEXT
port 32418 Acid Battery
port 32791 Acropolis, Rocks
port 33270 Trinity
port 33333 Prosiak
port 33545 G.R.O.B.
port 33567 li0n, T0rn Rootkit
port 33568 li0n, T0rn Rootkit
port 33577 Son of PsychWard
port 33777 Son of PsychWard
port 33911 Spirit 2000, Spirit 2001
port 34312 Delf
port 34313 Delf
port 34324 Big Gluck
port 34343 Osiris
port 34444 Donald Dick
port 34555 (UDP) - Trinoo (for Windows)
port 35000 Infector
port 35555 (UDP) - Trinoo (for Windows)
port 35600 SubSARI
port 36794 Bugbear
port 37237 Mantis
port 37651 Charge
port 38741 CyberSpy
port 38742 CyberSpy
port 40071 Ducktoy
port 40308 SubSARI
port 40412 The Spy
port 40421 Agent 40421, Masters Paradise
port 40422 Masters Paradise
port 40423 Masters Paradise
port 40425 Masters Paradise
port 40426 Masters Paradise
port 41337 Storm
port 41666 Remote Boot Tool , Remote Boot Tool
port 43720 (UDP) - KiLo
port 44014 Iani
port 44014 (UDP) - Iani
port 44444 Prosiak
port 44575 Exploiter
port 44767 School Bus
port 44767 (UDP) - School Bus
port 45092 BackGate Kit
port 45454 Osiris
port 45632 Little Witch
port 45673 Acropolis, Rocks
port 46666 Taskman
port 46666 (UDP) - Taskman
port 47017 T0rn Rootkit
port 47262 (UDP) - Delta Source
port 47698 KiLo
port 47785 KiLo
port 47785 (UDP) - KiLo
port 47891 AntiLamer BackDoor
port 48004 Fraggle Rock
port 48006 Fraggle Rock
port 48512 Arctic
port 49000 Fraggle Rock
port 49683 Fenster
port 49683 (UDP) - Fenster
port 49698 (UDP) - KiLo
port 50000 SubSARI
port 50021 Optix Pro
port 50130 Enterprise
port 50505 Sockets des Troie
port 50551 R0xr4t
port 50552 R0xr4t
port 50766 Schwindler
port 50829 KiLo
port 50829 (UDP) - KiLo
port 51234 Cyn
port 51966 Cafeini
port 52365 Way
port 52901 (UDP) - Omega
port 53001 Remote Windows Shutdown - RWS
port 54283 SubSeven , SubSeven 2.1 Gold
port 54320 Back Orifice 2000
port 54321 Back Orifice 2000, School Bus , yoyo
port 55165 File Manager trojan, File Manager trojan
port 55555 Shadow Phyre
port 55665 Latinus, Pinochet
port 55666 Latinus, Pinochet
port 56565 Osiris
port 57163 BlackRat
port 57341 NetRaider
port 57785 G.R.O.B.
port 58134 Charge
port 58339 Butt Funnel
port 59211 Ducktoy
port 60000 Deep Throat , Foreplay , Sockets des Troie
port 60001 Trinity
port 60008 li0n, T0rn Rootkit
port 60068 The Thing
port 60411 Connection
port 60551 R0xr4t
port 60552 R0xr4t
port 60666 Basic Hell
port 61115 Protoss
port 61337 Nota
port 61348 Bunker-Hill
port 61440 Orion
port 61603 Bunker-Hill
port 61746 KiLo
port 61746 (UDP) - KiLo
port 61747 KiLo
port 61747 (UDP) - KiLo
port 61748 (UDP) - KiLo
port 61979 Cool Remote Control
port 62011 Ducktoy
port 63485 Bunker-Hill
port 64101 Taskman
port 65000 Devil, Sockets des Troie, Stacheldraht
port 65289 yoyo
port 65421 Alicia
port 65422 Alicia
port 65432 The Traitor (= th3tr41t0r)
port 65432 (UDP) - The Traitor (= th3tr41t0r)
port 65530 Windows Mite
port 65535 RC1 trojan
3:41 PM | Labels: IP Addresses, Security | 0 Comments